Our tools monitor millions of native, push, pop, and TikTok advertising campaigns.
Get StartedRunning non-compliant ad campaigns is nothing new. Many online advertisers try to skirt the rules established by ad-networks to run campaigns that are not permitted by that ad-network. We see many examples of such campaigns on a daily basis on our spy platform.
The most commonly employed technique involves disguising the ad copy with text and images that don't raise any flags. This is followed by creating a fake or an innocuous landing page that is shown to the compliance team while directing the traffic to the actual money making page to the majority of audience. This is referred to as cloaking within advertising community.
Let's look at a hypothetical example. Online gambling is illegal in the United States. Therefore, an advertiser is prohibited from showing gambling ads to US audience as it is illegal. There are many offshore online gambling platforms that are looking for US based clients. So either they themselves or their affiliates will try to run such ad campaigns using cloaking techniques.
One of the earliest cloaking technique involved showing a compliant landing page during the campaign approval process and the URL was then redirected to a non-compliant page after the campaign was approved. As you can imagine, such a technique is very easy to detect and black-hat advertisers started coming up with more sophisticated techniques. This can include identifying "suspicious" traffic using visitor IP address, looking at http headers for inconsistencies, running javscript checks to see if the traffic is originating from a mobile device or an emulator etc.
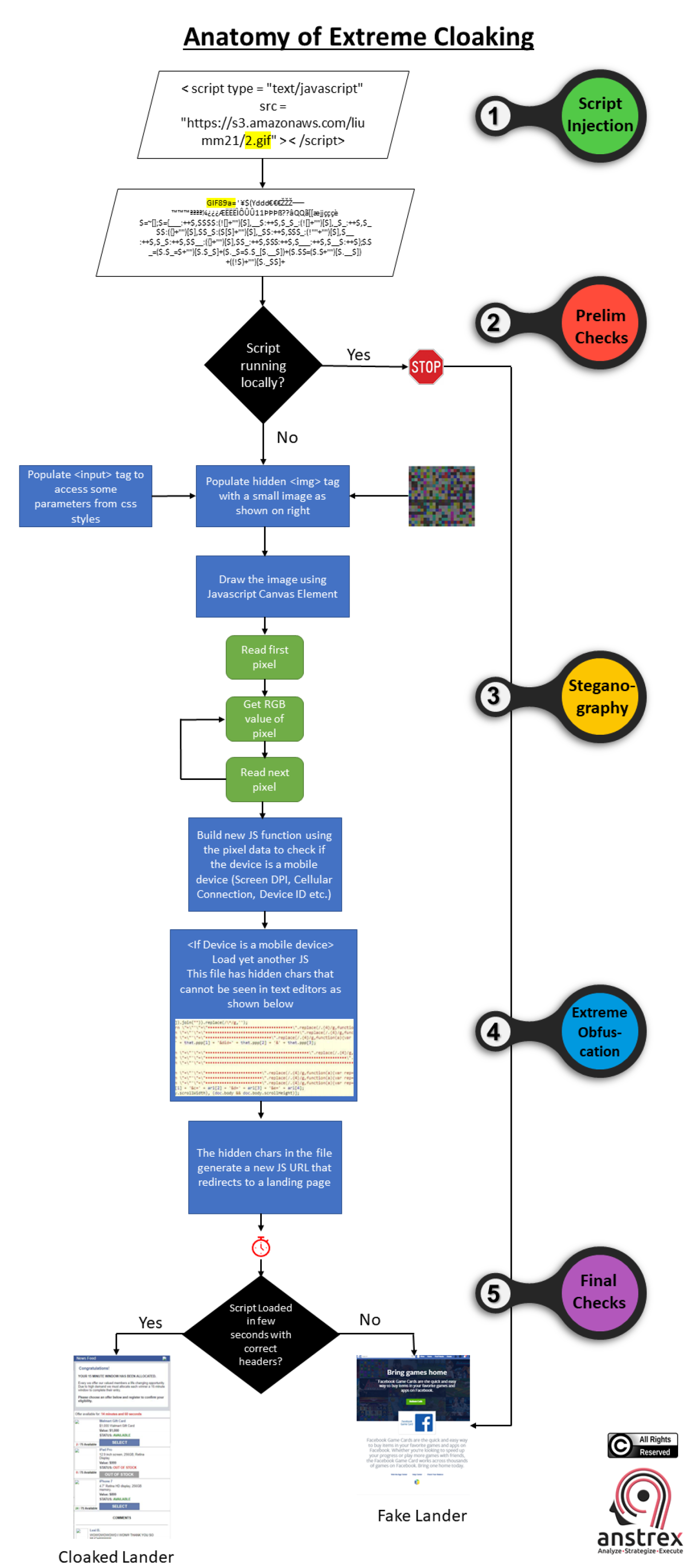
In this article, we are going to reveal one of the most complex and frankly jaw dropping cloaking technique that was first revealed by folks at bidfilter. It consists of multiple steps and checks that include some fascinating methods such as steganography, extreme obfuscation and clever javscript injection.
Before we detail the steps, let's take a look at the flow-chart below that makes it easier to understand the entire process:
Below are the links for the original whitepaper from bidfilter and high resolution pdf of the flow-chart, if you are interested.
White Paper: Original Whitepaper from BidFilter
Flowchart: High Resolution Flowchart in PDF format
As the author of the whitepaper noted, this by far is the most extreme example of the malicious ad serving that they have ever seen. I think it is safe to assume that this is not the last time we will see this. Ad-networks will have to step up their game if they are serious about fighting this kind of spam.
Receive top converting landing pages in your inbox every week from us.
Quick Read
Coordinating ads across multiple channels can significantly amplify your marketing ROI. Learn how to create a unified strategy that aligns messaging, timing, and targeting across platforms like Native, Push, and Pop. Discover how seamless cross-channel integration enhances brand recall and drives more conversions. Ideal for marketers aiming to make every ad dollar count through smarter coordination.
Marcus Chen
7 minDec 7, 2025
Case Study
TikTok has emerged as a powerful advertising platform for e-commerce businesses looking to drive sales and grow their customer base. This case study from Peru demonstrates the immense potential TikTok holds for e-commerce businesses.
Kulwant Nagi
7 minJul 14, 2024
Featured
TikTok is a key growth channel for Shopify in 2024. Start by adding the TikTok sales channel in Shopify, linking TikTok For Business, Business Center, and Ads Manager, and installing the TikTok Pixel with your chosen data sharing level. In Ads Manager, build campaigns → ad groups → ads, pick Product Sales (with a linked catalog), target by demographics/interests/behavior, and set a daily or total budget (often $20–$50 minimum). Test optimization goals—Clicks, Landing Page Views, and Conversions—to see what scales. Use short video creatives, Spark Ads, creator content via post codes, clear CTAs, and relevant keywords/hashtags. After approval, track analytics and iterate. For strategy, use Anstrex In-Stream to research competitors by filters, keywords, products, and stores, then model high-performing, demo-style, localized ads.
Jairene Cruz
7 minApr 25, 2024